Governing Objects from a Distance: Blockchains as Organizers of Environmentality
Of the phenomena in the field of media technologies that have conquered imaginations and funding buckets recently, blockchain technologies, next to artificial intelligence and machine learning, might be considered the most striking example. The blockchain constitutes a protocological internet layer for values that corresponds to a continuing monetization pressure and ongoing expansion of identification strategies. Notwithstanding these trajectories, behind this prospective killer application resides first of all a sovereign chronological regime that has the capacities to prove and modulate the existence, identity and administration of data, assets, goods and services from a distance on granular scales. [1]
As far as agency is concerned, the law holds that things and media are strictly passive. – Cornelia Vismann
One of the most common and important techniques since the advent of mass networked computing has been the basic computational operation to copy and paste. [2] To copy the contents from one address space to another in (networked) computers seems to be the one fundamental operation a networked society is relying on—on the technical level of computing itself and on the individual and societal levels of swapping clusters of larger files.
In the digital realm, the political concept of scarcity up until today proved too counter-intuitive and technically non-viable or too expensive to implement on a general scale. This became manifest in fundamental attacks endemic and systemic to digital cultures on property regimes, whose operationalization had formerly been intrinsically secured by the simple fact that consumers did not have the means to copy goods as they wished. [3]
The emergence of blockchain technologies is precisely the answer to the problem of digital non-scarcity. I argue that if there is one single capturing method that blockchain technologies are aiming at, it is to limit ubiquitous copying and pasting in a broad sense, i.e., to insert a digital proof of identity for data that may then be linked with appliances and other machines such as media players or access control via interfaces. “The business of embedding artificial scarcity into the digital asset is aligned with what appears to be an inevitable and continued enclosure of the mythos of the online commons within colonial apparatus” (Kaplinsky 2018, 269). The introduction of a time-stamped proof of existence within a presumably tamper-proof distributed ledger yields the late introduction of scarcity at the protocol level, almost fifty years after the introduction of TCP/IP (Transmission Control Protocol/Internet Protocol).
In the blockchain era, expected to be in full bloom within ten years, goods and services—physical or digital, manual or automated—are bound to a time stamp in the blockchain that is cryptographically secured. This time stamp marks the beginning of what might be called the post-digital, signified at its most basic function by remote, blockchain-based controls of existence. Property regimes, and other systems of control, may then be executed automatically by machines through permissionless (openly accessible), distributed ledgers, or permissioned (closed), centralized ones.
This text describes the very real possibility of this new kind of sovereignty—the sovereignty of the post-digital that modulates ownership and use of its commodities anew, from scratch. It can be understood as an extension and update of the bourgeois operating system, designed by the “vectorialist class” (Wark 2004). At its most radical trajectory, control shifts from external, non-digital, human-centered legal and administrative procedures, such as contracts, to internal, machine-centered and executable qualities of the commodities, goods and services themselves. Test cases and applications are already deployed in a variety of fields, such as the Porsche-XAIN project (see below) or, to randomly pick a use case where a blockchain legislates the existence of things, the Saudi customs service that tracks shipment movements with the aid of a blockchain. [4] Even if they fail in their first testing phases, the stakes are too high for possible emergent fine-grained monetization schemes and profits on new frontiers to not continue intensive research and development.
In short, blockchain regimes offer a robust and cheap technique for transfers of values and legislation of rights that excludes human interaction by setting up cryptographic trust between machines for value and rights administration. Its protocological design implements modulations of control over goods and services, often based on tokens, on an operational level. Tokens are the identity units of blockchains. They are currently popular as cryptocurrencies.
Proofs of Existence in Chronological Chains
A block in the blockchain contains a bundle of cryptographically signed transactions, like records in a ledger. Each block is linked sequentially to its predecessor so that the blockchain has a chronological order that constitutes a sovereign time-stamping regime. To implement this chronological regime in a decentralized peer-to-peer computing network can be seen as the most ingenious invention that blockchain techniques have integrated. [5] Once the ledger is updated with a new block containing transactions, agents (full nodes in the network), holding a copy of the blockchain, computationally either verify or falsify (reject) this addition, as they gossip the solution through the network, since it is peer to peer. A block that is verified by a protocologically designated number of agents becomes a permanent item in the chain, impossible to be removed or tampered with, since this would falsify all past computations of the blockchain, including the need to tamper with the majority of the distributed copies of the ledger.

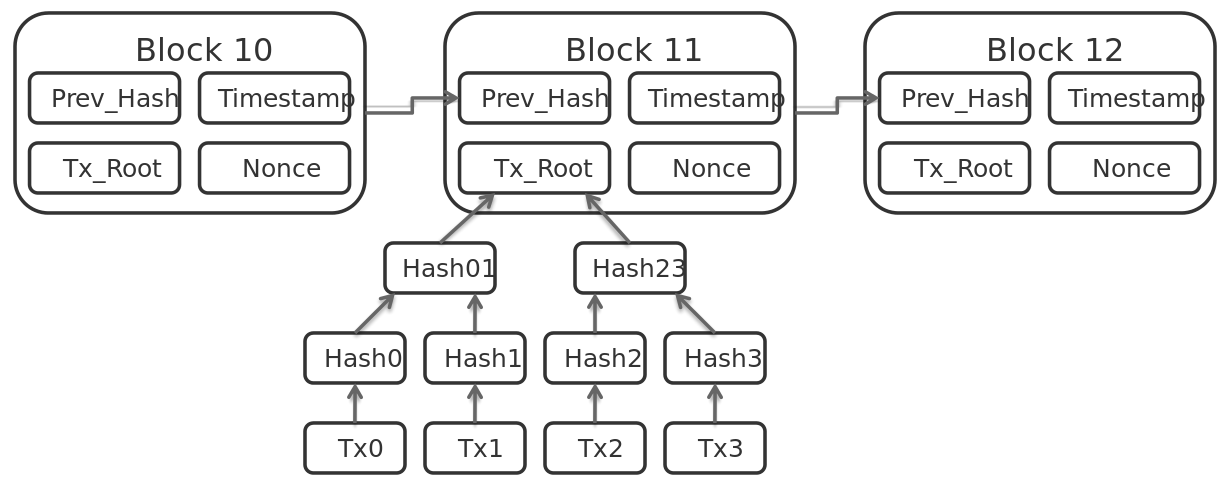
[Figure 1] Graphic of data fields in Bitcoin block chain. Simplified depiction. (Source: Matthäus Wander, wikipedia.org, CC-BY-SA 3.0 Unported)
The often-attested power of this mechanism resides in the parallelism of computation processes of nodes, each trying to solve hashing puzzles in order to compute the correct next block and thus forced into a competitive cooperation to find a “consensus” about which outcome of a reversed hashing operation is correct. Parallel computing is not used to distribute different processes over large clusters, but to distribute the same puzzle with a different set of variables over the network and to reward the first node to return the correct answer. Once a critical number of nodes agree on this answer, the chain has found its next block. The older this computational consensus becomes, the more it solidifies the structure. Trust is replaced with mathematical proof. [6]
The originality and limitation by design of such distributed databases is their append-only regime. All past elements are read-only and only the current block is a write operation. And furthermore, since the chain is secured in a backward direction via hashes, its complete verification (or falsification) is viable at any time by any node.
Hashes are mappings of data objects, usually large, most certainly [7] unique hexadecimal numbers. Hashes themselves do not reveal anything about the object (such as the block a hash refers to) except a one-way identification. By reproducing the hash with access to the hashed object, and checking it against the time-stamped hash in the blockchain, a proof of existence and identity is established that easily scales up to large numbers of objects. This is the basic mechanism referred to as “proof of existence” in the blockchain idiom. It can be applied to all sorts of data, objects, or processes. Blocks may contain hashes of a set of objects, or of other blockchain’s blocks. Put another way, the blocks contain registries of identification anchors for anything computable. This integration of object identifiers in a distributed database that is immutable through a forced consensus of chronologically ordered blocks in a chain is the basic building block for many further applications currently emerging.
Smart Contracts: Code for the Chain
One way to unleash the powers of blockchains are so-called smart contracts: code that runs “on top” (more precisely, in specialized virtual machines) of a blockchain to govern the execution of conditions, with sovereign access to assets and values registered in the chain. The idea to execute the terms of a contract with a transaction protocol dates back to 1994, when Nick Szabo, a prominent figure in the crypto-libertarian community, wrote a first conceptual paper by the same name, where he foresaw a reality that technically currently starts to unfold: “Smart contracts will replace, and even protect against, lawyers, politicians, and violent enforcement in many business and social interactions. They will also be used to design lucrative new free-market institutions” (Szabo 1994).
The Ethereum network, dubbed the first “world computer” by its inceptor Vitalik Buterin in 2013, was the first manifestation of a technology that combined the time-stamping regime of secured hashes with a Turing-complete programming language on a distributed computing platform, [8] and has since attracted billions of dollars in funding for projects running on its chain. The overwhelming majority of projects are issuing their own tokens that can be traded and thus it is most often exploited as a funding mechanism for (more or less shady) start-ups. Up until today, the Ethereum world computer remains “[t]otally unregulated and experimental in the extreme, Ethereum represents the true pirate utopia, equivalent to those of the corsair enclaves of the 16th century” (Vickers 2018, 234). [9] This became manifest when 100 lines of code raised $160 million in funding for the (failed) first D(ecentralized) A(utonomous) O(rganization). [10]
Land registries, real estate or royalty payments [11] are typical playgrounds for Ethereum-based attacks of markets that rely on middle-men authorities. Such attacks on established control mechanisms are basically proxying identification processes with cryptographically secured, automated trust. Smart contracts may be rather simple, such as non-disclosure agreements, but may also gain opaque complexity and obfuscate accountability since one may be nested into another, resulting in autonomous machines governing automated trades or acting as trading platforms themselves, such as EtherDelta. [12] Smart contracts rationalize administrative tasks, and by way of their immutable powers of execution one may agree that they are less prone to corruption or dysfunctional human-centered administrative structures. But this argument remains flawed, since software and coding themselves rest on a myriad of decisions, implicit assumptions, and error-prone coding by their producers. The neutrality of code is a well-maintained myth. Code functions discursively as a prolongation of instrumental reason, false objectivity, and obfuscation of power relations (Golumbia 2009), a fueling mechanism for the (ir)rationality that has been driving capital expansion ever since (Haraway 1997). This holds true all the more for blockchain technologies, as Adam Greenfield, amongst others, points out: “in its design, important questions about human interaction, collaboration and conviviality are being legislated at the level of technological infrastructure” (Greenfield 2017, 117). Interestingly, the advocates of smart contract-based transfers of value see the position of the middle man being eliminated, while in reality its agency has been transferred to those who control the development of code and protocol. This does not alter the argument that smart contracts have considerable powers once executed, but the position of control has shifted and changed.
Smart contracts offer intriguing opportunities for different unfoldings of events. Since the execution of a smart contract is guaranteed (or rather: immanent to its existence), the possible futures of the contract become a calculable, hedged present, paving the way for a new contract working on the present future captured. Smart contracts, in other words, naturally trigger more smart contracts by setting up executable loops from a captured future in the present, juggling with different time loops that again may have executable passages into new foldings. Of course, this is nothing new per se, since finance products such as derivatives gain their powers from the manipulation and foldings of time or, in other words, from an antagonistic relation towards the real and its monetary value at some point in time (Lee and Martin 2016). But if smart contracts “render decisions in the present on situations that were conceptualized at some arbitrary point in the past” (Greenfield 2017, 172) without any implemented interface to update or correct them according to the present real, then they run the risk of becoming ignorant, detached from the chaotic unfolding of this real and thus brutal, unstoppable executioners of value passages. Agnostic and automated, they are prone to have a considerable impact on this unknown real, and as such they—as machines—are gaining ontological powers, or ontopowers, to borrow a term from Brian Massumi (2015).
The displacement of human interaction based on trust towards machines is inherently antisocial and driven by technologist thought. But then again, whatever this “Nerd Reich” (Vickers 2018, 237) may develop into, there are powerful organizations and administrations in the way of its full, frictionless bloom. Ethereum as “a Bretton Woods for our time” (Vickers 2018, 237) might never become true in this totalitarian sense.
Besides these speculations on the coming right-wing libertarian technologist insurrection, vast differences between the complex social practices that are part of contracting practices and the machinic form proposed by smart contracts already exist today. Contracts are—broadly speaking—social resources to manage relations amongst people and not technical artifacts. Karen Levy reminds us that “contractual obligations are enforced through all kinds of social mechanisms other than the legal system proper; concomitantly, contracts serve many functions that are not explicitly legal in nature, or even designed to be formally enforced” (Levy 2017, 5). Considering the many aspects of common contracts that are (up until today) non-intelligible to and (by design) excluded from smart contracts, one may question if smart contracts do really “allow us to construct contracts that mimic other contracts” (Szabo 1994)—this mimicry has at least a profound bias and is reductionist in nature.
On the other hand, the term smart contract itself maybe should not be taken too literally, in terms of being neither “smart” nor a “contract.” The novelty of this automatically effectuated code in the realm of values still lacks its discoursive determination and needs further discussion. For instance, being “book smart” (Levy 2017, 10) points towards a genealogy of bookkeeping, not contractual law. Nonetheless, there are kinships to be excavated. Cornelia Vismann in her genealogical discussion of the operational status of files for the legal apparatus states that “[t]he inquiry into the origin of the law leads. . . to administrative record keeping” (Vismann 2008, 4). And folders became the self-processing medium that automated order. “Folders instructing users where they should be brought next literally get files on their way (Vismann 2008, 138). Vismann’s argument is that the sovereignty of media starts in administration—which is a main target of blockchains today. They are tools to administrate values and assets.
But administrative bookkeeping does not begin to cover the complexities that smart contracts can handle. Since computational powers and distributed data processing are native to smart contracts, their affiliation is much more with data-based targeting and discrimination. What Louise Amoore described as data derivatives (Amoore 2011)—risk trades based on inferences about who we might be, derived from of all kinds of data—in conjunction with smart contracts become an automated, fully data-driven speculation machine with access to wealth and values.
The attack vector of smart contracts on established legal and economic practices through their utterly technologist design and human- and institutional-decentric trajectories is a weapon and a vehicle for the vectorialist class to tap wealth and assets directly, since:
[t]heir power lies in monopolizing intellectual property—patents, copyrights and trademarks—and the means of reproducing their value—the vectors of communication. The privatization of information becomes the dominant, rather than a subsidiary, aspect of commodified life. (Wark 2004, 32)
Smart contracts are a solution to automate this hyper-commodification process and redistribution of wealth into new class sub-formations. It is the market and private property that are targeted and effectuated at once. [13] This comes with a fine but important difference to the stratified system. “Lex Cryptographia” (Wright and De Filippi 2015)—as this emerging regime might be dubbed—are “almost always those of capital, of property. From financial restrictions, through shares and deeds, into contracts and ‘intellectual property.’ But this law is set free from its bourgeois state shackles—and checks and balances” (Myers 2018, 246).
What is more, by way of smart contracts and proofs of existence laid down in blockchains, the gap between symbolic orders and the real diminishes further and opens up the possibility of automated governance of physical spaces and things, too. Taking up the seminal notion Bruno Bosteels put forth in his discussion of Felix Guattaris a-signifying semiotics (Bosteels 2001, 899): smart contracts as codified truth work “flush with the real.” The execution of code as performative, a-signifying semiotics has fused with the distribution and administration of values.
Micro-administration of Goods and Services from a Distance as a Control Paradigm of Environmentality
The remaining part of this article will focus on the order of property and its administration via blockchains. This field has not seen much consideration although it is here that blockchains are developing into an environmental power (Massumi 2015, 22–27; Hörl 2018). Governmentality (Foucault 2007, 2008) has largely been understood as a means to govern from a distance, by producing a set of options for subjects to decide upon in a market-driven environment. Its main target, in the Foucauldian genealogical account, is the production of subjects that govern themselves and see themselves as entrepreneurs of themselves, even if all they can bring to the market is their labor time. Blockchain technologies complement political technologies to govern from a distance, with the important difference that the targets are not subjects but objects. This extension of governing from a distance is mastered by way of an “objectification” of the current property regimes, fusing them with the objects themselves, as I will explain in the remaining parts of this contribution.
The advent of clusters of blockchains has met the advent of the Internet of Things—not only historically, but strategically, too. Physical objects, especially those that provide access or modulate it, and the amalgamation of items with networking capacities into everyday objects, is in full swing and might become the new normal for large parts of the urban classes and their management of social relations. Nick Szabo called this “smart property,” which “might be created by embedding smart contracts in physical objects” (Szabo 1994). The smartphone as the universal access device has been integrated into all prospective customers’ agency already. From renting bikes to paying for lunch cash is on the retreat, and we are in a kind of testing phase about which financial protocol to implement for our most mundane commercial activities. I agree that, “it is through the blockchain that the Internet of Things will acquire the ability to exchange access permissions for payment, and via the Internet of Things the gradients of access will be inscribed on the physical world” (Greenfield 2017, 155).
Blockchains answer a problem that transforms all individual addressability from the ground, or, even better, they for the first time unfold it to the level of a permanent environmental management of control. For a better understanding of this emerging order of things, let us turn to the historical unfolding of the current property regime, because its solidification was not without troubles and frictions. It needed to be flanked by laws that are modulated by morals in order to gain full traction when for the first time in history the distribution of wealth became too uneven and at the same time too visible to be left to its own devices.
It is the invention of liberal society and its securing mechanisms by a whole new set of laws that Michel Foucault, in his 1972–73 lectures on the punitive society, analyzed in terms of a bourgeois morality as a modulation of laws in the fields of ownership and property. He identified a betrayal at work, as property owners, once they had established their property regimes through theft (such as the theft of the commons and their transformation into private property, or the slave trade), appropriated theft itself as a class-dividing element in their penalty system. Thus, he connects this bourgeois betrayal on the possibility of theft with a method to govern the labor force that owns nothing but their labor time. But prior to this capture of theft and betrayal by the favored of the bourgeois revolution, theft was considered a means at hands for anyone involved in the toppling of the feudal society:
It seems to me that until the end of the eighteenth century a certain lower-class illegalism [illégalisme populaire] was not only compatible with, but useful to, the development of the bourgeois economy; a point arrived when this illegalism, functionally enmeshed in the development of the economy, became incompatible with it. (Foucault 2015, 140–141)
These illégalismes populaires included practices of stealing from the feudal classes and were in alliance with the bourgeois revolution. But once the revolution was over and became sedimented into the bourgeois order they posed a threat to the bourgeois society itself, resulting in moral-modulating laws instantiated thoroughly and exclusively against the have-nots. This resembles to a large degree the digitalization efforts and establishment of networking capacities for the masses in our last decades, as they were strongly supported by all kinds of “media piracy” practices on a large scale, like downloading, and effectively establishing a new way to distribute cultural goods for the working poor globally (cf. Sundaram 2009; Fredriksson and Arvanitakis 2014). Foucault’s originality here lies in his description of the “hack” that allowed the new bourgeois regime to install its new class-divisional penalty system: “Thus, if the Code does not allow itself to punish in the name of the moral law, it provides for the possibility of punishing according to morality, which is thus a moral modulation of the law” (Foucault 2015, 177).
The triad of theft, property and betrayal resembles Proudhon’s notion “property is theft,” a reference Foucault does not state. In addition, it has a certain parallel to the infringements of intellectual property and patents in the nineteenth century, when US companies were stealing blueprints for production from European countries before the US was an established world power and long before it condemned China for doing the same (Ben-Atar 2004).
Today, in digital cultures, the triad of property, betrayal and theft extends its problematic beyond the originally only physical distribution of goods into an area that until recently kept the political concept of property and of use in an unalterable state of artificiality. The digital realm requires a quasi-counterintuitive mental operation regarding the problem of theft, because the question of ownership and use here decouples itself from the concrete product. A digital product, whose existence and identity is not related to production or consumption, since it can be copied (a non-rival product), challenges any moral-modulating law system that differentiates its own operations of betrayal positively by modulating theft negatively, as Foucault remarked (2015, 175–200). The relation between an excess of goods here and their lack somewhere else had up until now found its most pressing problematic in the digital realm, where the political concept of scarcity remained mostly unknown. Rights violations, on the other hand, have been a catalyst for the dissemination of the internet within large parts of the population by way of illegal downloading, and as such have been a welcomed aspect in the establishment of a networked society; however, in the long run they are too problematic and care-intensive for the current order of property and ownership. Digital goods lack existence and identity in the sense of a physical object and thus digital stolen goods are not stolen, because stealing conceptually means a loss for someone else (rivalry). This non-identity of the commodity, as a produced single item, and its unlimited possibilities of distribution do not match the criteria established previously for physical commodities. Digital commodities are, as seen by the property regimes that Foucault describes, damaged commodities from the start, although they are not compromised as a product. Until now, the anonymous mass practice of unlawful (re-)distribution of digital goods profited from the fact that digital products are non-identifiable in their existence as single objects.
The blockchain reworks these mismatches on the level of the condition of the commodity itself. Digital artifacts that have been made discriminable and identifiable by a cryptographic time-stamp of existence in a blockchain re-adjust the bourgeois order of betrayal and theft in favor of the bourgeois betrayal once again. By discriminating formerly non-discriminable data, a mode of registration of digital objects is introduced that at the same establishes a new regime of control. With the introduction of the concept of digital existence, a new parametric modulation of its ontological status has become operative. For instance, in this set-up “stolen” digital goods would lose their functionality since their legal status is negative. We can see a process of development from the damaged commodity to the damaged product.
Within this trajectory, the use or consumption of a commodity is bound to conditions that do not have to be defined outside of the commodity, in a contract stating the acquisition and, with it, the rights to use it, but they move, so to say, into the interior of a commodity through control over its functionality. The blockchain is the trusted ledger from which the conditions of use are defined, modified and unlocked. With this object orientation, a blockchain can, for instance, lock a stolen product from a distance and render it (data) trash—a damaged good. Further, the user of such a smart physical product may only interact with the object within a range of possibilities defined by the ownership data in a blockchain. “Smart” in this context signifies an encroachment of exterior control beyond the acquisition of the commodity into the time of its use. This resonates with the so-called sharing economy, which is aiming at a commodification regime of use values.
Such an “acquisition until revocation” or “acquisition under limited conditions” establishes an operational extension of the initial bourgeois betrayal on property—as described by Foucault—into the time of consumption, and eliminates the possibility of theft by non-legally acquiring parties. It is this basic operation of use control that renders (digital) objects insusceptible to theft and illegal use. By way of a historical entanglement of two fundamental axioms of the bourgeois order—the impossibility of distinguishing single instances of digital objects (the problem of a non-rival product) and the masking of their historicity through the commodity form—the question of ownership “retreats” into the object itself via its hashed anchors in the blockchain and overcomes its naturally agnostic relation to property regimes due to its ontological status. Blockchain technologies merge the proof of ownership and rights administration with the object itself on a technological level and set this level as primary. They “objectify” the property regime by capturing things throughout their lifetime and oversee them as if this regime was inseparable from the object itself. This operation might be termed a technological objectification of social relations.
What may sound like a dystopian future of control to some has already found its way into the patent application system and forged collaborations of new partners. To name just one example Porsche is collaborating with Berlin-based start-up XAIN to model access control and tracking of traffic data into a blockchain for each individual car: “Unlocking your Porsche car happens via an online transaction that is mined by the vehicle network.” [14] Of course, this administration of things from a distance is not viable for every little physical item—but almost everything: Lenovo has filed a patent to track changes in paper documents during their life cycle with a blockchain application (Kapinos et al. 2018). Such an application targets the problematic of trust in a world of adversaries and competitors by delegating authenticity to machines, causing a undisputable chain of changes in the workflow of administrations and offices.
In general terms, we can discover two elements within this described evolutionary path of a technologically controlled rights regime for objects. First, the technology of identity and governance, as the blockchain signals it, which finds, secondly, its physical technological counterpart in the so-called Internet of Things. This path contains management and logistics strategies that aim at an automated administration of things from a distance. The blockchain secures the order of bourgeois property and ownership relations, and at the same time develops it for new modulations of control. Governing from a distance acquires new meaning in light of blockchain-based access and use regulation for things and services. In a sense, property relations are now becoming a functional aspect or dimension immanent to goods and services, as they become integrated into the objects. The powers of a multitude of blockchains governing objects are not only performative and prescriptive on the level of object administration, but at the same time constitute a hard and fixed time regime that contains and structures these objects and their possible use. Fixing use dates or establishing time frames of use are a natural outcome of an autonomous chronological regime.
What is more, if we contextualize this “objectification” of bourgeois property regimes as an attempt to govern objects from a distance, an analysis of power has to integrate this novel perspective, too. When the establishment of the industrial age was governed by the production of docile bodies through the regimes of discipline, it targeted the individual but not the subject with its mentalities. The production of subjects that would internalize their own government according to markets and entrepreneur behavior became the cornerstone of the twentieth century’s focus, identified with neoliberal endeavors and termed governmentality by Foucault. The current shift of modulation towards objects and their government signals at least two things: first, a crisis in the production of subjectivity, and second, the becoming environmental of power. Orchestrating the government of subjects and objects from a distance signifies a new phase of capture and control, made possible by ubiquitous computing, a networked society, and the distributed ledgers that blockchains are offering.
References
Amoore, Louise. 2011. “Data Derivatives: On the Emergence of a Security Risk Calculus for Our Times.” Theory, Culture & Society 28 (6): 24–43.
Ben-Atar, Doron. 2004. Trade Secrets: Intellectual Piracy and the Origins of American Industrial Power. New Haven, CT: Yale University Press.
Bianconi, Andrea. May 8, 2018. “Opinion: Calm before the Storm? The Coming Crackdown on ICOs.” www.ccn.com/opinion-calm-before-the-storm-the-coming-crackdown-on-icos/.
Bosteels, Bruno. 2001. “From Text to Territory: Félix Guattari’s Cartographies of the Unconscious.” In Deleuze and Guattari: Critical Assessments of Leading Philosophers, edited by Gary Genosko, 881–910. London/New York: Routledge.
DuPont, Quinn. 2018. “Experiments in Algorithmic Governance: A History and Ethnography of ‘The DAO,’ a Failed Decentralized Autonomous Organization.” In Bitcoin and Beyond: Cryptocurrencies, Blockchains and Global Governance, edited by Malcolm Campbell-Verduyn, 157–177. Abingdon/New York: Routledge.
EtherDelta. 2019. Accessed June 23, 2019. https://etherdelta.com.
Ethereum Developers. June 17, 2019. “A Next-Generation Smart Contract and Decentralized Application Platform.” https://github.com/ethereum/wiki/wiki/White-Paper.
Foucault, Michel. 2007. Security, Territory, Population: Lectures at the Collège de France, 1977–78. Basingstoke/New York: Palgrave Macmillan.
Foucault, Michel. 2008. The Birth of Biopolitics: Lectures at the Collège de France, 1978–79. Basingstoke/New York: Palgrave Macmillan.
Foucault, Michel. 2015. The Punitive Society: Lectures at the Collège de France 1972–1973. Edited by Bernard E. Harcourt and Graham Burchell. Basingstoke/New York: Palgrave Macmillan.
Fredriksson, Martin and James Arvanitakis. 2014. Piracy: Leakages from Modernity. Sacramento, CA: Litwin Books.
Golumbia, David. 2009. The Cultural Logic of Computation. Cambridge, MA: Harvard University Press.
Greenfield, Adam. 2017. Radical Technologies: The Design of Everyday Life. London/New York: Verso.
Haraway, Donna Jeanne. 1997. Modest−Witness@Second−Millennium.FemaleMan−Meets−OncoMouse: Feminism and Technoscience. London/New York: Routledge.
Hörl, Erich. 2018. “The Environmentalitarian Situation.” Cultural Politics 14 (2): 153–173.
Kapinos, Robert James, Timothy Winthrop Kingsbury, Scott Wentao Li, and Russell Speight VanBlon. 2018. Verifying Integrity of Physical Documents. United States Patent US9922278B2, filed August 15, 2016, and issued March 20, 2018.
Kaplinsky, Helen. 2018. “Collections Management on the Blockchain: A Return to the Principles of the Museum.” In Artists Re:Thinking the Blockchain, edited by Marc Garrett, Ruth Catlow, Sam Skinner, and Nathan Jones, 261–274. London: Liverpool University Press.
Lee, Benjamin and Randy Martin. 2016. Derivatives and the Wealth of Societies. Chicago: University of Chicago Press.
Leistert, Oliver. 2019. “Kontrolle ist gut, Vertrauen ist besser, Bezahlung am besten: zur Souveränität von Blockchains.” Zeitschrift für Medien- und Kulturforschung, 2: in print.
Leistert, Oliver. 2018. “On the Question of Blockchain Activism.” In Routledge Companion to Media and Activism, edited by Graham Meikle, 376–384. London/New York: Routledge.
Leistert, Oliver. 2013. “Mietmodell Software Adobe.” POP: Kultur und Kritik. 3 (2): 39–42.
Levy, Karen E. C. 2017. “Book-Smart, Not Street-Smart: Blockchain-Based Smart Contracts and The Social Workings of Law.” Engaging Science, Technology, and Society 3 (February): 1–15.
Massumi, Brian. 2015. Ontopower: War, Powers, and the State of Perception. Durham, NC: Duke University Press.
Myers, Rob. 2018. “Blockchain Poetics.” In Artists Re:Thinking the Blockchain, edited by Marc Garrett, Ruth Catlow, Sam Skinner, and Nathan Jones, 239–250. London: Liverpool University Press.
Nakamoto, Satoshi. 2009. “Bitcoin: A Peer-to-Peer Electronic Cash System.” Accessed June 23, 2019. https://bitcoin.org/bitcoin.pdf.
Porsche Digital Lab. March 23, 2018. “The Porsche-XAIN Vehicle Blockchain Network: A Technical Overview.” https://medium.com/next-level-german-engineering/the-porsche-xain-vehicle-blockchain-network-a-technical-overview-e1f48c40e73d.
Rajamanickam, Vishnu. May 22, 2019. “Saudi customs pilots shipment movement via blockchain.” Freight Waves. www.freightwaves.com/news/saudi-customs-pilots-shipment-movement-via-blockchain.
Richmond, Jill. May 9, 2017. “How Blockchain Technology Can Transform Royalty Payments.” https://www.nasdaq.com/articles/how-blockchain-technology-can-transform-royalty-payments-2017-05-09.
Sundaram, Ravi. 2009. Pirate Modernity: Delhi’s Media Urbanism. London/New York: Routledge.
Szabo, Nick. 1994. “Smart Contracts.” Accessed June 23, 2019. https://web.archive.org/web/20011102030833/http://szabo.best.vwh.net:80/smart.contracts.html.
Vickers, Ben. 2018. “Immutability Mantra.” In Artists Re:Thinking the Blockchain, edited by Marc Garrett, Ruth Catlow, Sam Skinner, and Nathan Jones, 233–237. London: Liverpool University Press.
Vismann, Cornelia. 2008. Files: Law and Media Technology. Stanford: Stanford University Press.
Wark, McKenzie. 2004. A Hacker Manifesto. Cambridge, MA: Harvard University Press.
Wikipedia (en). 2019. The DAO (organization). Accessed June 23, 2019. https://en.wikipedia.org/wiki/The_DAO_(organization).
Wikipedia (en). 2019. Hash Function. Accessed June 23, 2019. https://en.wikipedia.org/wiki/Hash_function#Uniformity.
Wright, Aaron and Primavera De Filippi. March 20, 2015. “Decentralized Blockchain Technology and the Rise of Lex Cryptographia.” https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2580664.
Endnotes
[1] I cordially thank the editors for their fine feedback and precise comments.
[2] “Copy and paste” is an operation commonly associated with a graphical user interface (GUI). Included in the meanings here are all basic instructions, such as “cp” in the *nix world, and those executed in programs, scripts, by daemons or called by other programs. “Paste,” seen from a *nix perspective, is just the second parameter of “cp,” i.e., the target.
[3] Recently, strategies to solve this problem of digital non-scarcity have shifted towards streaming and in general towards access-based models. Adobe was amongst the first of the big software companies to offer their products on a subscription basis only (Leistert 2013). My argument is that the blockchain model is a strategy to operationalize scarcity digitally and thus to (finally) introduce it into the digital realm as a naturalized attribute derived from physical objects.
[4] Rajamanickam, Vishnu. May 22, 2019. “Saudi customs pilots shipment movement via blockchain.” Freight Waves. https://www.freightwaves.com/news/saudi-customs-pilots-shipment-movement-via-blockchain.
[5] The original proposal for Bitcoin, the first manifestation of a distributed ledger, sketches its concept in a few pages (Nakamoto 2009). Its authors and inventors are unknown; Satoshi Nakamoto is a pseudonym. For a thorough discussion of decentralized consensus protocols and their proposals of sovereign media, see Leistert 2019.
[6] Such a Proof of Work algorithm has seen contenders recently, optimized to tackle issues of energy consumption or scalability, amongst other things. In a way, Bitcoin can be seen as a role model that instigated an immense research and development process in industry, finance and individuals that are motivated to participate in the hacking of money. As of today, the number of blockchains at work is already impossible to estimate. For instance, Amazon, the biggest cloud computing company, recently offered blockchain-based functionalities (Ethereum or Hyperledger based) to cloud computing customers as a templated extra bundle. See: https://aws.amazon.com/blockchain/templates/.
[7] The chances that a hash maps more than one object appear to be negligible. See https://en.wikipedia.org/wiki/Hash_function#Uniformity.
[8] See the continuously updated white paper (Ethereum Developers 2019).
[9] Initial coin offerings (ICO), phrased after initial public offerings (IPO), the mechanism invoked when a company goes public and will be traded on stock exchanges, are beginning to be chased by the empire, to remain in the metaphor from Vickers. The finance regulation bodies are tightening the conditions that have to be met globally for an ICO. This very unregulated phase of ICOs is already history. See Bianconi, Andrea. May 8, 2018. “Opinion: Calm before the Storm? The Coming Crackdown on ICOs”. https://www.ccn.com/opinion-calm-before-the-storm-the-coming-crackdown-on-icos/.
[10] The first DAO, a collection of smart contracts, was an investor-directed venture capital fund. Bugs in the code allowed for a redirection of large parts of its huge funds. See https://en.wikipedia.org/wiki/The_DAO_(organization). But if code really is law, as the maximalists of the libertarian technologists claim, then this was not at all an illegitimate action, but only poorly coded law. For a thorough reconstruction of this incident, see Quinn DuPont’s “experiments in algorithmic governance” (2018).
[11] Richmond, Jill. May 9, 2017. “How Blockchain Technology Can Transform Royalty Payments.” https://www.nasdaq.com/articles/how-blockchain-technology-can-transform-royalty-payments-2017-05-09.
[12] See EtherDelta 2019. See the operational code here: https://etherscan.io/address/0x8d12a197cb00d4747a1fe03395095ce2a5cc6819#code.
[13] For more on if and how blockchains might be of use beyond the assumption that value has to be quantified and put under the regime of the general exchange equivalent, see my discussion of the Economic Space Agency in Leistert 2018.
[14] Porsche Digital Lab. 2018.